OPSWAT Packet flow and
Troubleshooting:-
Netscaler 10.5 we have noticed the
new feature of OPSWAT Editor. It's just like the same EPA we have earlier but
with some extra features from 3rd Party OPSWAT.
Before you begin make sure your
client machine has the Root CA of the AGEE vserver under Trusted Root CA
certificate on your machine else it will fail in the initial check itself
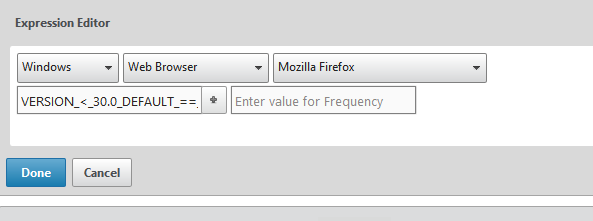
To configure OPSWAT just go to the
OPSWAT editor and give the expression you like
Here I am testing for some
expression as below
First expression is checking if
Internet Explorer is running or My system domain belongs to
"WrongDomain" or My mozilla firefox browser should be my default
browser and must be above version 30.0.
CLIENT.APPLICATION('BROWSER_60000_RUNNING_==_TRUE[COMMENT:
Internet Explorer]') EXISTS ||
CLIENT.SYSTEM('DOMAIN_SUFFIX_anyof_WrongDomain[COMMENT: Domain check]') EXISTS
|| CLIENT.APPLICATION('BROWSER_61000_VERSION_>_30.0_DEFAULT_==_TRUE[COMMENT:
Mozilla Firefox]') EXISTS
The configuration part is pretty
simple in the OPSWAT as you can see it's easy to understand. As I did for my
Mozilla firefox check
Now it's time to Test this.
In my system from which I am
trying it has Internet explorer running, Mozilla firefox is default browser and
is of version 32.0 but my domain is not "wrongDomain" this I did
intentionally so this check should fail. But overall it should pass since my
expressions has 3 expressions and if any one of them match then Netscaler will
allow me to access.
Go to my AGEE Page and it prompted
for the EPA plugin scan , I clicked YES
After this I got prompted for the
AGEE credentials which means my scan is successful
Let's see the reason why, So that
you can troubleshoot yours.
Before Reproducing the issue make
sure you do the following things
1.
Disable SSL session
reuse from the AGEE vserver otherwise you won't be able to decrypt the trace.
You can enable it afterwards
2.
Make the following
changes in your client Registry for the OPSWAT log collection( it won't harm in
anyway)
HKEY_LOCAL_MACHINE\SOFTWARE\Citrix\Secure
Access Client
Make a
DWORD value with "EnableEPALogging" and set the value to 1
3.
Now start the trace on
Netscaler and reproduce the problem
4.
After that go to
command prompt run as administrator and go to
C:\Program
Files\Citrix\Secure Access Client
And run
the command
nsClientCollect.exe
<path where you want to save the outputfile\<filename.zip>
So the Logs are collected.
Analyzing the Logs:-
Wireshark:-
The Typical Packet Flow look like
this
·
You send a GET / to
the AGEE
·
Get redirected to 302
for the epa.html page
·
Next Get is for
epa.html page followed by a 200 OK
·
Then client send the
GET/ epatype for which the Netscaler replies with the type of epa being
performed. In my case it's just epa and no device cert hence that is off
·
Then comes the major
packet called GET/epaq where client request for the type of scan to be
performed
As you can see in the below highlighted that the NS replied with the scans to
be performed
First check is for Mozilla browser
version should be above 30.0 and should be default
Second is my domain should be
"Wrong Domain"
Third my browser must be running
Internet explorer
Before running these scans the
client check with netscaler about the OPSWAT library version. If it matches
then it continues otherwise it will download the new version from Netscaler. In
our case it same so no downloads
In the Next request the Netscaler
sends back it's epa scan result. Always 0 means successful and non zero means there is a failure
In my scenario
First check is for Mozilla browser
version should be above 30.0 and should be default----- Passed so value 0
Second is my domain should be
"Wrong Domain"--- Failed since I don't belong to this doman value 3
Third my browser must be running
Internet explorer----- Passed since my Internet explorer is running, Value 0
So I got the CSEC header value as
030 as you can notice below
Since in my Netscaler the
condition is to allow if any one of them matches hence I got a 200 OK with
value 10
For e.g. In case of failure scenario
the expression will fail and you will see following in the response as 00.
So getting a 10 is our main
concern and avoiding 00
Client Logs Analysis:-
When you will extract the Output
file you will notice the following files. Out of which highlighted are our
concern ( if you don't see epaHelper_epa_plugin file then that means you forgot
to enable Registry value as mentioned above or it's wrongly given)
In epaHelper_epa_plugin file you
can see all your result
Adv. EPA Scan log file
Date: 09/18/2014
Time: 23:42:22
=========================
23:42:22.500 Successfully parsed
tokens
23:42:23.125 Oesis framework init
SUCCESS
23:42:23.268 Version value 32.0.1
, expected 30.0
23:42:27.127 Scan Passed ( So
Mozilla firefox scan passed, since my version is 32.0 which is above 30.0)
23:42:27.127 Successfully parsed
tokens
23:42:27.127 Domain is lab.net
23:42:27.127 Scan failed for Scan
method SUFFIX ( Here its failed since my domain is lab.net but I Netscaler
tried to search for Wrong Domain)
scanQuery :
DOMAIN_SUFFIX_anyof_WrongDomain
23:42:27.127 Successfully parsed
tokens
23:42:27.200 Scan Passed
If you need more detailed analysis
then you can go for nsepa logs which will give you the same information as I
told you in wireshark. Most important is to check the CSEC value as you can see
it's 030 here.
23:42:27.201
<GET epas HTTP/1.1
Cookie:
NSC_EPAC=********************************
CSEC: 030
post body information is hidden
>
23:42:27.217 FQDN of the server is
agee.com
23:42:27.217 downloaded total 118
bytes
23:42:27.217 ns_HTTPrequest return
value is: 118
23:42:27.217 Received headers size
80
23:42:27.217 ns_start_epa
returning passed
Important Notes as of
10.5 build:-
·
In device cert check
is present then there will be one extra value EPA type ON and Device Cert ON
·
Except for Device Cert
auth , Epa package upgrade or running doesn't need admin right.
In OPSWAT scan,EPA plugin will check what version is there on Netscaler, If
Netscaler version is above then the installed on client then it will ask
for new library
with
GET /epapackage and will install the new epaPackage
·
To check the OPSWAT
EPA library you can got to following director of Netscaler and check the
version.xml file
/netscaler/ns_gui/epa
root@NG10#
more version.xml
<?xml
version="1.0" encoding="UTF-8"?>
<Windows>
<EPALib>1.1.1.8</EPALib>
</Windows>
root@NG10#
·
In mac the client logs
are situated at Library/Appliation support/citrix/epa plugin/epaplugin.log (
You don't have to run any command to collect logs)
·
Netscaler at present
has a limit of 1499 characters for expressions including all the fields of the
expression from starting till end
In case
you have a requirement then to overcome this by creating new policies
·
CSEC value limit is
25K of buffer. So if the scan CSEC value took more than 25K of buffer normally
in mac address scan then scan will fail
·
To upgrade the OPSWAT build no need of Netscaler
upgrade is required.